- Why RedFlag
- Solutions
-
Problems We Solve
RedFlag Mass Notification Platform
Communication Features
Send Real-Time Alerts that Get Attention
Multi-channel alerts including text, email, voice calls, MS Teams, app notifications and moreUtilize Desktop Alerts
Reach hard-to-reach workers on laptops, desktops, or shared monitors and workspacesEmpower Two-Way Chatting
Engage in multiple one-to-one conversations via text messagingGet Insights with Action-Based Messages
Direct feedback with polling and acknowledgmentManage
Precise Targeting with Groups
Easily create prederminted segments or on the fly with any data points including real-time GPS locationEasy Data Management + Syncing
Easily upload and keep data clean with FTP, API options including Azure sync and more
-

Not if, But When: Best Practices for Creating a Cyber Security Plan

October 21, 2021 Posted by Pocketstop in Crisis Communications, Business Continuity Social Share
Whether you’re a Fortune 50 company or a small business, cyber criminals are attacking companies of all sizes and becoming more brazen and destructive as a result. The stats bare this out:
- Cybercrime is up 600% year-over-year due to the COVID-19 pandemic – even small businesses saw a 424% increase in cyberattacks last year
- The average cost of an attack to small organizations was $7.68 million
- 45% of SMBs say that their processes are ineffective at mitigating cyber attacks
In order to protect your business, it is important to put the right cyber security plans into place to minimize and mitigate a cyber attack while maintaining clear lines of communications with your employees, vendors, and stakeholders.
Cyber Security Plans – The Problem
Cybercrime is not always the high-profile event we see on the news. Very often breaches are the result of an internal misstep that results in security being compromised, rather than a malicious, intentional attack. Even when bad actors gain access to a system, they do not always steal – instead the purpose may be to disrupt your business (another type of cost to be sure).
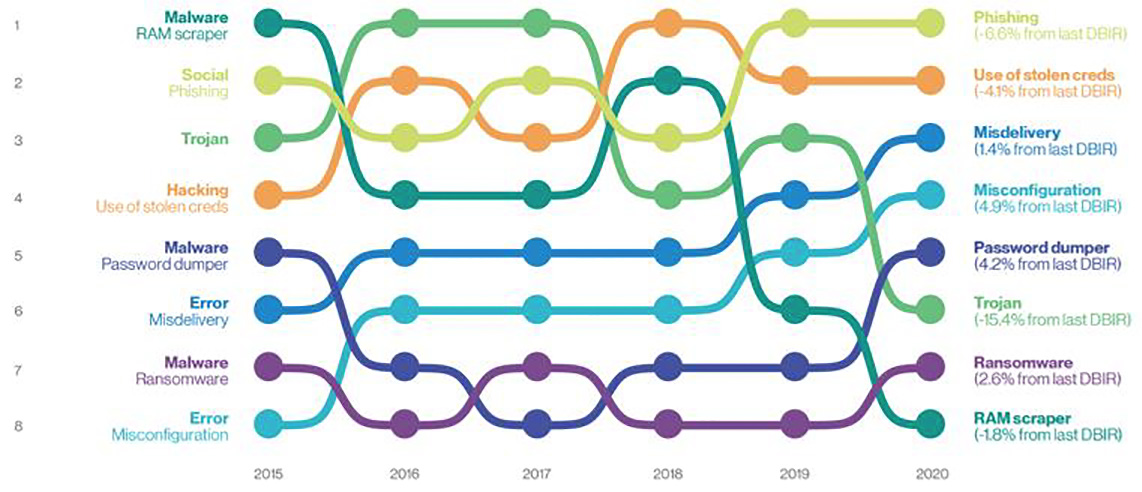
cyber security incident timetable
While there are numerous security software solutions, the problem is they are often built as a one-size-fits all, which does not in the end protect an organization. These tools might be better used as part of a specific plan developed in-house, provided there is someone knowledgeable to advise which of the hundreds of choices will work best for you.
Cyber Resiliency – Making Your Own Plan
Not surprisingly, the best way to weather such an event is to have a robust cyber security plan in place that everyone knows how to execute. Unfortunately, such plans are often not prioritized until it’s too late, and then the only thing to do is react.
Taking the time to create a 3 area plan can ensure that when a breach occurs the damage is minimal.
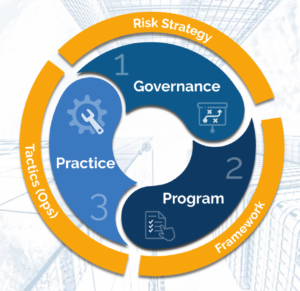
Cyber Security 3 Area Plan
First, an organization should design its Risk Strategy to include policies, procedures, and compliance metrics. This lays a solid foundation for the next stage, which is a Framework for responding. This area includes the more granular steps that will be taken, who will complete them, and when. And finally, the practical aspects of implementing the strategy that include tactics and operations.
Rather than only examining a cyber security plan after the fact, it is critical to revisit it on a regular basis so that it is continuously improving. This is especially true with cyber threats, as they change constantly.
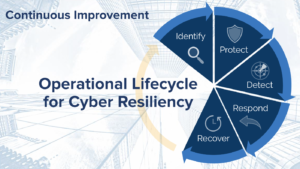
Cyber Security Lifecycle
Performing an audit is a good way to begin. Use the audit to identify risks, gaps, and assets. This should include penetration testing, incidence response, data privacy, and identity management. Next, design a detailed plan to protect your organization. This includes training and awareness, encryption, network security, endpoint, logical security, tracking (logs, monitors, alerts), application security, and database security. This step should ensure that you can detect threats in real time and launch the response sequence to isolate and neutralize any threats. And finally, recover from the incident not only by repairing and replacing what was lost, but also evaluate the entire process.
While having a well-thought-out cyber security plan in place is the best way to protect against catastrophic loss or disruption, training and awareness is also key. If employees do not know how to recognize or report suspicious events, valuable time is wasted and numerous opportunities will present themselves to hackers.
When the Inevitable Occurs – Crisis Communication
Part of your practical response during a cyber attack will be communication. Just as with all the other aspects, it is best to have a solid plan ready.
During a crisis, you will want to leverage multi-channel notification capabilities to ensure recipients immediately get the message. Communicate on the crisis and the immediate actions needed or being taken, as well as the impact of the crisis and next steps. As you plan potential communications, be sure to consider multiple audiences:
- Victims (priority)
- Internal employees
- Customers
- Suppliers
- The press
If there is a system compromise or outage, you will be able to utilize another system for communication that does not depend on your internal capabilities, like Redflag mass alert software. With this software, you will be able to send out real-time notifications in seconds via multiple channels of communication, such as text, voice call, Microsoft Teams messages, etc.
Drafting potential messages as part of your plan before an attack happens shows quick decision making ability and will help your team feel more confident and calm. Keep these tips in mind as you create communications:
- Write clear, short, jargon-free messages
- Determine who the victims are and show solidarity with them and eagerness to find solutions
- Be transparent about the incident and its consequences
- Send the right message
- “We know:” we know there has been a cyber incident;
- “We do:” we are working on the following solutions;
- “We care:” we understand the gravity of the situation and we care about the victims;
- Important, – “We are sorry:” we apologize for this malfunction;
- And finally –“We will be back:” we will keep you informed.
Something to remember in the bigger picture: in challenging moments, unity matters more than ever. A close second is how to learn from a challenging situation – what can be done better, and how will it be accomplished? Even a very good cyber security plan can be improved for next time.
This information is taken from the webinar Hackers Gonna Hack: Establishing Cyber Security Protocols for the Inevitable. Click this link to watch the webinar replay.
About Pocketstop
Pocketstop is a communication software solutions company who empowers companies to create personalized, automated messages designed to provide rapid ROI backed by the industry’s best support at a cost customers can afford. Our commitment to excellence propelled us to become the industry’s pioneer in innovative and effective technologies with a portfolio of customer-focused products designed to drive audience behavior, improve efficiency, provide insight and actionable data for decision making by improving their existing internal, employee, stakeholder or customer communication strategies. For more information, visit https://pocketstop.com.
About Filos Technology
Filos Technology wants to help you conquer your technology roadmap. Our certified engineers are dedicated to finding best-in-class solution at the best price, while creating a seamless implementation process from start to finish, and beyond. Our team is able to equip IT professionals with in-depth provider market research to help with vendor selection, oftentimes shifting dollars back into our clients IT budgets.
We offer strategy and consulting, interactive technology, hardware, and operations services—all powered by a large network of industry-leading technology solutions. https://filostechnology.com/
Ready to Get Started?
See how RedFlag can help you protect what matters most with a 15-minute custom demo.
